- Ensuring robust EOR data security is critical for protecting your global workforce against evolving cyber threats and maintaining full regulatory compliance in 2025 and beyond.
- Top Employer of Record providers maintain compliance with major data privacy laws like GDPR, CCPA, and other regional regulations to safeguard employee data worldwide.
- A comprehensive EOR security framework includes industry-standard encryption, multi-factor authentication (MFA), strict role-based access controls, and regular security audits to prevent breaches.
- Effective EORs implement transparent employee data lifecycle management by minimizing data collection, securing storage, and facilitating employee rights such as data access, correction, and deletion.
- Continuous compliance monitoring, vulnerability assessments, and detailed incident response plans enable rapid breach containment and ensure ongoing adherence to global data protection standards.
Ready to simplify your global hiring? Contact Wisemonk today!
Discover how Wisemonk creates impactful and reliable content.
Looking for robust EOR data security for your global team? As businesses expand globally, managing employee data across different countries becomes a complex challenge. The need for strong data protection measures is more critical than ever, especially with the rise of evolving threats and stricter regulations. Navigating this complex landscape requires a deep understanding of compliance and a proactive approach to information security. In this guide, we’ll explore the key aspects of EOR security and data protection, ensuring your data is handled securely and in full compliance with global data privacy laws.
How do EORs handle data protection regulations?[toc=Data Protection Regulations]
Expanding internationally means you're stepping into a world with a patchwork of different data protection laws. From Europe's strict rules to the varied approaches in the US, understanding and complying with these regulations is paramount. Let's break down some of the most significant frameworks that top-tier EORs must navigate to keep your sensitive data safe.
General Data Protection Regulation (GDPR) Requirements
The General Data Protection Regulation (GDPR) is the gold standard for data protection globally, even for businesses outside of Europe. It dictates strict requirements on how personal data of European citizens must be collected, processed, and stored. For an EOR to be truly GDPR compliant, they must:
- Lawful Basis for Processing: They must have a legal basis for processing personal data, such as explicit consent from employees or a contractual necessity.
- Data Minimization: Only the data that is necessary for the intended purpose should be collected.
- Data Subject Rights: Employees have the right to access, rectify, and erase their data, as well as the right to data portability. EORs must have clear processes to handle these requests.
- Data Protection Officer (DPO): Organizations handling large amounts of sensitive information must appoint a DPO to oversee data protection strategy and ensure compliance.
CCPA and other regional privacy laws
While GDPR sets the benchmark, other regions have their own significant data privacy laws. The California Consumer Privacy Act (CCPA) gives consumers, including employees, in California more control over their personal data. Key aspects for EORs to consider include:
- Right to Know and Delete: Employees have the right to know what data is being collected and to request its deletion.
- Non-Discrimination: Companies cannot discriminate against employees who exercise their CCPA rights.
Beyond the US and EU, many countries have their own specific requirements, from Brazil’s LGPD to Canada’s PIPEDA. A leading EOR will have a global legal team to ensure they meet the specific legal requirements in each country where they operate.
Cross-border data transfers
One of the biggest challenges for a global EOR is the secure transfer of data across borders. This is a critical area of EOR security. When transferring data from the EU to a third country, the EOR must ensure adequate safeguards are in place. This often involves:
- Standard Contractual Clauses (SCCs): These are pre-approved contracts by the European Commission that provide safeguards for data transfers.
- Binding Corporate Rules (BCRs): These are internal rules approved by EU data protection authorities for multinational corporations to transfer personal data within the same corporate group.
Consent management
Consent is a cornerstone of many modern data privacy laws. While not always the primary legal basis for processing employee data (as it can be subject to power imbalances), when it is used, it must be:
- Freely Given: Employees must give consent without any pressure.
- Specific and Informed: The purpose for which the data will be used must be clearly stated.
- Unambiguous: Consent must be a clear, affirmative action.
What does a robust EOR security framework look like?[toc=EOR Security Framework]
A top-tier EOR doesn't just talk about data security; they build their entire business processes around it. This requires a multi-layered approach that secures data at every stage of the employee lifecycle. It’s about more than just having good intentions; it's about the implementation of a comprehensive security framework designed to withstand modern cyber threats.
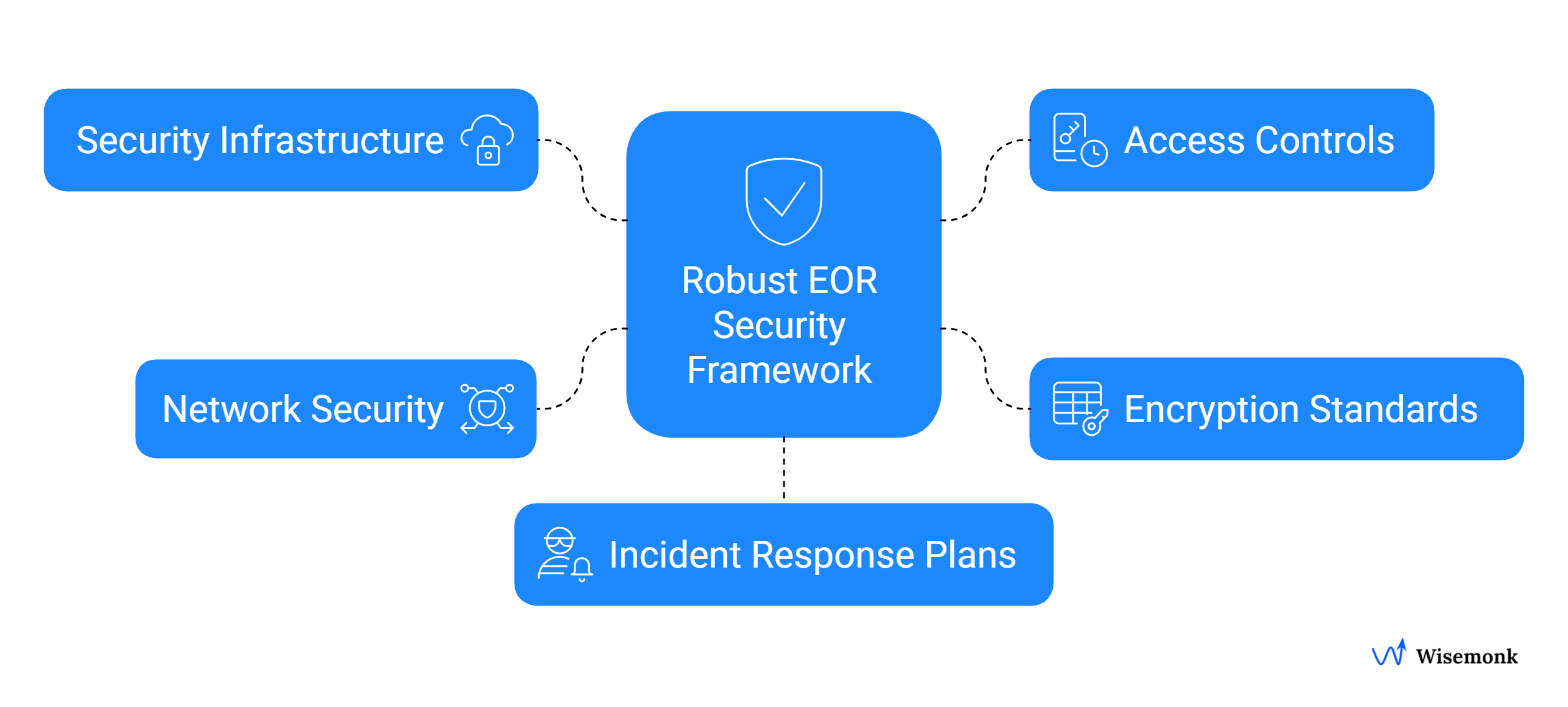
- Security Infrastructure: A strong EOR relies on a secure cloud infrastructure, often leveraging providers like AWS or Azure. This includes using firewalls, intrusion detection systems, and network segmentation to prevent unauthorized access. Regular updates and patching are non-negotiable to protect against security breaches and evolving threats.
- Access Controls: This is the bedrock of any information security policy. Access to sensitive data is granted on a "need-to-know" basis. A leading EOR will use a combination of technologies like Multi-Factor Authentication (MFA) and Role-Based Access Control (RBAC) to ensure that only authorized personnel can access specific personal data. These measures are in place to protect sensitive information from internal and external threats.
- Encryption Standards: For data to be truly safe, it must be encrypted both "at rest" (when it's stored) and "in transit" (when it's being sent between systems). EORs should use industry-standard encryption protocols like AES-256 for data at rest and TLS 1.2+ for data in transit. This makes the data unreadable to anyone without the proper decryption key, offering a vital layer of protection.
- Network Security: This involves protecting the EOR's network from all angles. It includes not just firewalls, but also secure VPNs, anti-malware software, and proactive monitoring to identify suspicious activity. A secure network is crucial for maintaining business continuity and preventing data breach incidents.
- Incident Response Plans: No matter how good your security is, the potential for a data breach always exists. A comprehensive data breach response plan is essential. This plan should detail the steps to take in the event of a security incident, including containment, notification of affected parties, and a clear path to recovery. Having this in place demonstrates a commitment to rapid and effective data protection.
How does an Employer of Record manage employee data?[toc=Employee Data Management]
Effective employee data security goes beyond just preventing breaches, it’s more about a comprehensive strategy for managing personal data throughout the entire employment relationship. A top-tier EOR ensures that every step of the data processing journey is handled with the utmost care and in full compliance with global data protection laws.
- Data Collection Practices: A responsible EOR only collects the data that is absolutely necessary for legal and business purposes. Transparency with employees about what private data is being collected and why is a must.
- Storage and Retention Policies: An EOR must have a robust system with country-specific retention rules, ensuring sensitive information is stored securely for the required period and then disposed of properly. This is a core component of strong data protection measures.
- Access Permissions: Access to employee data must be tightly controlled. The principle of least privilege ensures that only authorized personnel can access different types of data, like bank information.
- Employee Rights Management: Under laws like GDPR, employees have specific rights regarding their personal data, including the right to access, correct, or delete it. An EOR must have streamlined processes to handle these requests promptly.
- Data Portability Requirements: A compliant EOR must be able to provide the employee's data in a structured, machine-readable format if a company decides to switch EOR providers, respecting the employee's right to data portability.
How do EORs monitor compliance?[toc=Compliance Management]
Maintaining EOR data security is an ongoing process, not a one-time setup. It requires constant vigilance and proactive measures to ensure compliance with a constantly changing regulatory environment. A truly effective EOR will have a robust system for continuous monitoring and verification to protect your company and your employees from potential risks.
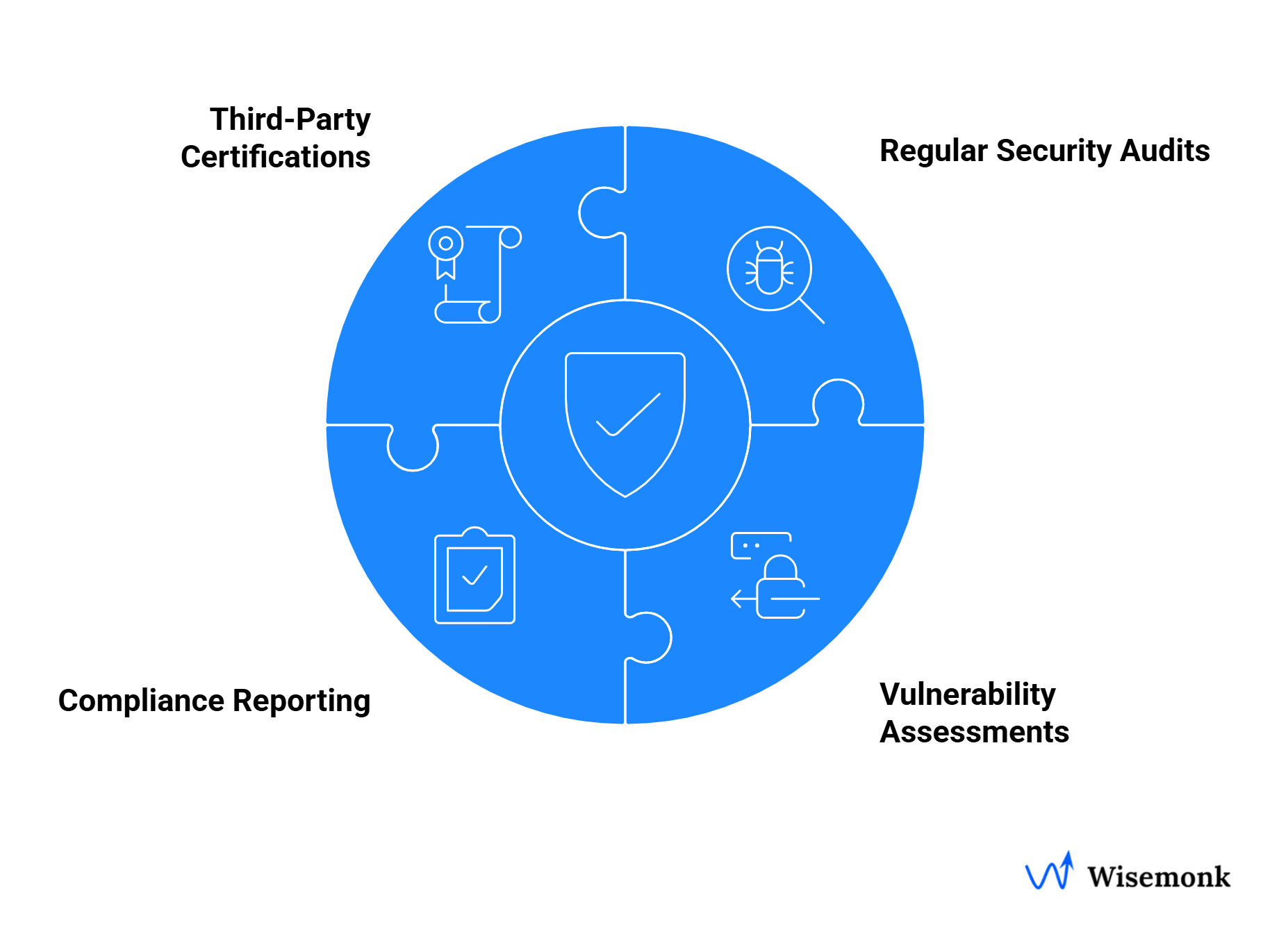
- Regular Security Audits: A top-tier EOR conducts frequent internal and external security audits. These regular audits are vital for maintaining high standards of information security and for demonstrating compliance to clients.
- Vulnerability Assessments: Beyond routine audits, a proactive EOR will perform regular vulnerability assessments and penetration testing. These risk assessments simulate a real-world attack to identify and fix potential entry points for a data breach.
- Compliance Reporting: For a global company, having clear documentation is essential. A leading EOR provides detailed, regular compliance reports to their clients, offering a transparent view of their security posture and how they are meeting their legal obligations.
- Third-Party Certifications: Look for an EOR that holds recognized third-party certifications, such as ISO 27001. These certifications are a powerful indicator of a company's commitment to information security and data protection. They signify that the EOR has been independently verified to meet strict international standards for managing sensitive information.
How do EORs identify and mitigate security risks?[toc=Security Risk Mitigation]
A proactive approach to EOR data security means not just reacting to threats but actively identifying and addressing potential risks before they can cause harm. For a leading EOR, this is a core part of their business processes, ensuring the continued protection of sensitive data and maintaining business continuity. Based on our experience, we have seen that a detailed and ongoing risk management strategy is non-negotiable for anyone handling personal data on a global scale.
- Security Risk Identification: This is the first step in a robust risk assessment. An EOR must systematically identify a broad range of risks that could threaten information security. This includes everything from cyberattacks and internal threats to physical security vulnerabilities and compliance gaps. It requires a thorough analysis of all systems, processes, and data flows to pinpoint weaknesses.
- Impact Analysis: Once a risk is identified, the next step is to analyze its potential impact. An EOR must assess the severity of the harm a successful attack could cause. This isn't just about financial loss; it also includes the potential for regulatory fines, reputational damage, and, most importantly, the impact on employee privacy. A data protection impact assessment (DPIA) is a key tool for evaluating these risks.
- Mitigation Strategies: With a clear understanding of the risks and their potential impact, an EOR develops specific strategies to mitigate them. These can include a variety of security measures like implementing stronger encryption, enhancing access controls, or improving employee awareness programs. The goal is to reduce the likelihood and/or the impact of a given risk to an acceptable level, ensuring the data remains safe.
Conclusion[toc=Conclusion]
Wisemonk is a leading Employer of Record service provider and your strategic partner for seamless workforce expansion and compliance. From compliant hiring to payroll, contractor management, and benefit administration, Wisemonk handles every aspect of talent management so companies can focus on scaling, without the need for a local entity. Our comprehensive solutions include:
- Employer of Record (EOR): Hassle-free hiring, onboarding, payroll, tax compliance, and benefits for employees.
- Payroll & Compliance: Local payroll processing, pay slips, and statutory filings (PF, ESI, PT, TDS) across India.
- Contractor Management: Agent of Record (AOR), unified contractor payments, GST/tax filings, and freelancer compliance.
- Recruitment Services: End-to-end talent acquisition, screening, and selection for specialized roles.
- Global Capability Centers (GCCs): Support for setting up and managing offshore centers and permanent teams in India.
- Additional Services: Benefits, insurance, office setup, smooth exits, settlements, and ongoing HR compliance.
Whether entering new markets, managing payroll, or streamlining contractor payments, Wisemonk's blend of technology, compliance, and local expertise makes global workforce management frictionless and secure. Ready to accelerate your global hiring or workforce operations? Contact us today!
Frequently asked questions
How do EOR providers ensure employee data security?
Top EORs ensure employee data security through a multi-layered approach. This includes using secure, encrypted cloud infrastructure, strict access controls on a "need-to-know" basis, and regular vulnerability assessments. They also implement comprehensive information security policies and employee training to prevent a data breach.
What certifications should EOR providers have for data protection?
To demonstrate a commitment to data protection, EORs should hold relevant third-party certifications. The most recognized and important one is ISO 27001, an international standard for managing information security. This certification confirms that an EOR has a systematic approach to managing and protecting sensitive data.
How is employee data transferred securely between systems?
Secure data transfer is critical for preventing a data breach. EORs use industry-standard encryption protocols, such as TLS 1.2 or higher, to secure data "in transit." This ensures that any personal data exchanged between your company's systems and the EOR's platform is fully encrypted and unreadable to unauthorized parties.
Can employees request deletion of their data from EOR systems?
Yes, under regulations like GDPR and CCPA, employees have the "right to be forgotten." A compliant EOR must have clear processes in place to handle these requests. They are required to delete an employee's data upon request, unless there is a specific legal or contractual reason to retain it.
What happens to employee data if we switch EOR providers?
If you switch EOR providers, your former EOR is obligated to securely handle the transition of your employee's data. The original EOR must provide the personal data in a structured, commonly used format, as required by data privacy laws like GDPR's right to data portability. The new provider is then responsible for securely ingesting and managing the data going forward, ensuring continued compliance.
How do EOR providers protect against cyber threats and data breaches?
Top EOR providers implement multi-layered security measures including advanced encryption, multi-factor authentication (MFA), regular security audits, and vulnerability assessments to prevent unauthorized access and cyberattacks. They also maintain comprehensive incident response plans to quickly contain and remediate any data breaches, minimizing risk to employee information and business operations.
What ongoing compliance measures do EORs take to ensure data privacy?
Leading EORs continuously monitor regulatory changes globally and conduct frequent internal and third-party audits to maintain compliance with laws such as GDPR, CCPA, and local data protection regulations. They implement strict data minimization, retention policies, and vendor management protocols to ensure employee data is handled securely throughout its lifecycle.

.png)
%20(1).webp)